Border Roaming Monitoring With IOT Platforms

R&D Corner
-
Border roaming refers to the use of mobile devices to connect to a foreign mobile network operator (MNO) while traveling abroad. When a mobile device roams internationally, it typically connects to the foreign MNO’s network through a border roaming gateway, which acts as an intermediary between the device and the foreign network. This allows the device to access voice and data services while traveling abroad.
Border roaming is used to facilitate international roaming and allow mobile devices to connect to foreign networks and access services while traveling outside of their home network coverage area.
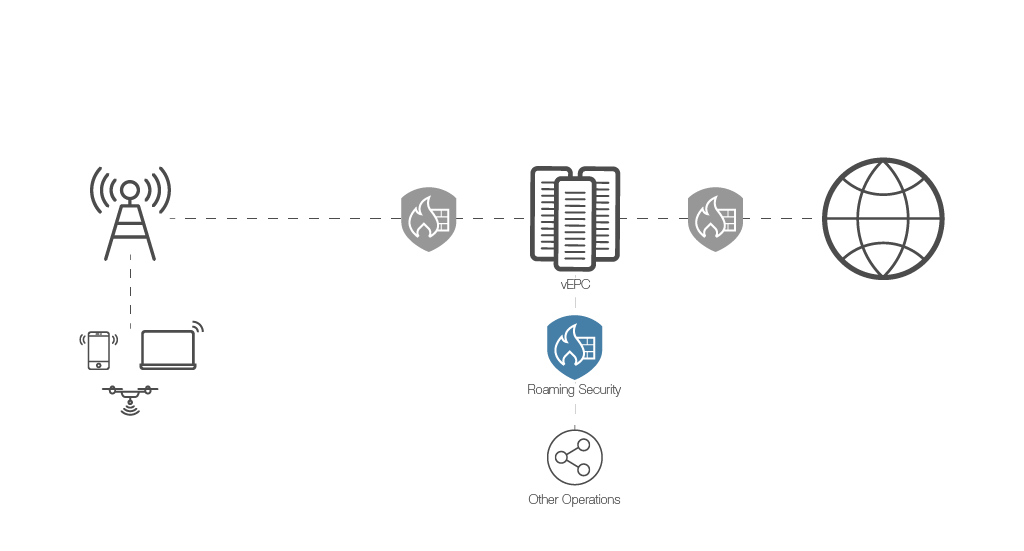
A border roaming gateway is a network device that enables mobile devices to seamlessly connect to a foreign mobile network while roaming outside of their home network coverage area. It is used to facilitate international roaming by providing a connection between a mobile device and a foreign mobile network operator (MNO).
The border roaming gateway acts as an intermediary between the mobile device and the foreign MNO, allowing the device to connect to the foreign network and access voice and data services. When a mobile device roams internationally, it typically connects to the foreign MNO’s network through the border roaming gateway. The gateway acts as a “gateway” between the two networks, allowing the mobile device to connect to the foreign network and access the services it needs.
The border roaming gateway plays an important role in facilitating international roaming, as it enables mobile devices to connect to a foreign network and access voice and data services while traveling abroad. Without the border roaming gateway, mobile devices would not be able to connect to a foreign network and would be unable to access voice and data services while roaming internationally.
There are several problems that can arise with border roaming in a Global System for Mobile Communications (GSM) network. Some of these problems include:
- Billing issues: One common problem with border roaming is the high cost of using mobile services while traveling abroad. This can lead to unexpected charges on the user’s bill, which can be a source of frustration.
- Network connectivity issues: Mobile devices may have difficulty connecting to a foreign network while roaming, leading to dropped calls and poor quality of service.
- Compatibility issues: Mobile devices may not be compatible with the foreign network, which can lead to connectivity issues and reduced functionality.
- Security concerns: Mobile devices may be vulnerable to security threats while connected to a foreign network, such as data breaches or malicious attacks.
- Regulatory issues: Different countries have different regulations and policies regarding mobile services, which can lead to issues with border roaming.
Border roaming gateway security refers to measures that are taken to secure the connection between a mobile device and a foreign mobile network operator (MNO) through a border roaming gateway. These measures are designed to protect against potential security threats that could compromise the confidentiality, integrity, and availability of the mobile device and the data it handles.
Some examples of border roaming gateway security measures might include:
- Encryption: Encrypting the connection between the mobile device and the foreign MNO through the border roaming gateway can help to protect against data breaches and unauthorized access to sensitive information.
- Authentication: Implementing strong authentication protocols can help to verify the identity of the mobile device and prevent unauthorized access to the network.
- Firewall protection: Using a firewall to block unauthorized access to the network can help to prevent malicious attacks and other security threats.
- Intrusion detection and prevention: Implementing intrusion detection and prevention systems can help to detect and prevent unauthorized access to the network.
Overall, border roaming gateway security is an important consideration to protect against potential security threats and ensure the confidentiality, integrity, and availability of mobile devices and data while roaming internationally.
There are several things that a GSM user can do to prevent roaming while on a border:
- Turn off data roaming: One option is to turn off data roaming on the mobile device. This will prevent the device from connecting to a foreign network and accessing data services while traveling abroad.
- Use a local SIM card: Another option is to purchase a local SIM card and use it in the mobile device while traveling abroad. This will allow the device to connect to the local network and access services at local rates, rather than roaming rates.
- Use a virtual private network (VPN): A VPN can be used to encrypt the device’s internet connection and prevent it from connecting to a foreign network. This can be a useful way to prevent roaming while on a border.
- Use a roaming prevention app: There are various apps available that can help prevent roaming while on a border. These apps can be used to block the device from connecting to a foreign network or to redirect the device to a preferred network.
- Contact the mobile carrier: It may be possible to work with the mobile carrier to set up a plan or package that allows for border roaming without incurring high charges. This can be a good option for frequent travelers.
By following these steps, a GSM user can prevent roaming while on a border and avoid unexpected charges and connectivity issues.
It is possible to design an Internet of Things (IoT) system to monitor the border network and analyze the stats of registrants to detect if they are registering with other countries’ operators by mistake. Such a system could potentially provide several benefits, including:
- Improved connectivity: By detecting and correcting errors in network registration, the system could help to ensure that mobile devices remain connected to the appropriate network and have access to the desired services.
- Reduced costs: By preventing accidental roaming, the system could help to reduce costs for mobile users who might otherwise incur high charges for roaming services.
- Enhanced security: By detecting and preventing unauthorized access to foreign networks, the system could help to enhance the security of mobile devices and protect against potential threats such as data breaches or malicious attacks.
However, it is important to note that implementing such a system would require careful planning and consideration of various technical, regulatory, and legal issues. Additionally, the system would need to be regularly maintained and updated to ensure that it remains effective and reliable over time.
An IoT system that monitors the border network and analyzes the stats of registrants to detect and prevent accidental roaming could potentially be useful and serve as a business model. Such a system could provide value to mobile users by helping to ensure that they remain connected to the appropriate network and have access to the desired services while minimizing costs and enhancing security.
To determine the feasibility and potential success of such a system as a business model, it would be necessary to conduct market research to assess the demand for such a service and evaluate the competitive landscape. Other factors to consider would include the costs of developing and maintaining the system, the potential revenue streams and pricing models, and any regulatory or legal considerations.
Overall, an IoT system that helps to prevent accidental roaming could be a useful and potentially viable business model, depending on the specific circumstances and market demand.
There are various types of artificial intelligence (AI) that could potentially be implemented in an IoT system that monitors mistaken roaming. Some examples might include:
- Machine learning: Machine learning algorithms can be used to analyze data and identify patterns or trends that could indicate a mistake in network registration. By learning from historical data, the system could potentially improve its accuracy over time.
- Natural language processing: Natural language processing algorithms could be used to analyze user feedback and identify common issues or problems with network registration. This could be particularly useful for detecting and correcting mistakes that are made by users who are unfamiliar with the local network or language.
- Predictive analytics: Predictive analytics algorithms could be used to forecast the likelihood of a mistake in network registration based on various factors such as location, device type, and user behavior. This could help the system to proactively prevent mistakes before they occur.
Ultimately, the specific type of AI that would be most suitable for an IoT system that monitors mistaken roaming would depend on the specific requirements and goals of the system, as well as the available data and resources.
